Protecting Critical Infrastructures From Cyber Attack And Cyber Warfare Zones

: The Rising Threat Landscape
4.6 out of 5
| Language | : | English |
| File size | : | 13512 KB |
| Print length | : | 363 pages |
| Screen Reader | : | Supported |
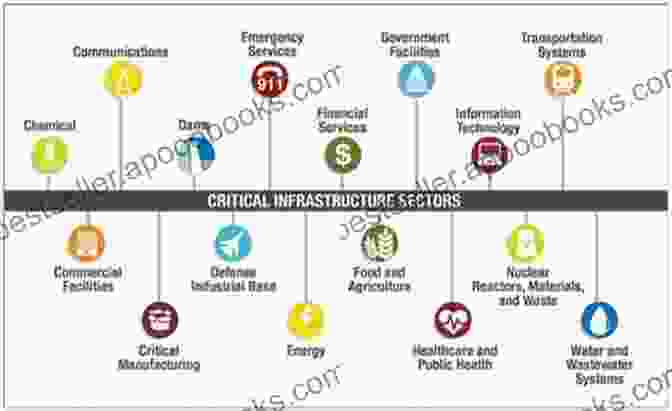
In the modern interconnected world, critical infrastructures are the backbone of our society and economy. These systems, including power plants, water treatment facilities, transportation networks, and communication systems, are essential for maintaining public health, safety, and well-being.
However, with the rise of cyber threats and the increasing sophistication of cyber attackers, critical infrastructures have become a prime target for malicious activity. Cyber attacks can disrupt or even disable these systems, causing widespread damage and disruption.
In this comprehensive guide, we will explore the threats facing critical infrastructures, discuss strategies and technologies for defending against cyber attacks, and provide actionable insights for protecting these essential systems.
Chapter 1: Understanding the Cyber Threat Landscape
1.1 Types of Cyber Attacks
- Malware: Malicious software that can damage or steal data.
- Phishing: Scams designed to trick individuals into revealing sensitive information.
- Ransomware: Software that encrypts data and demands a ransom payment for its release.
- Distributed Denial-of-Service (DDoS) attacks: Attacks that overwhelm systems with traffic, making them inaccessible.
1.2 Cyber Attackers and Their Motives
- Cybercriminals: Seek financial gain through data theft or ransomware attacks.
- Hacktivists: Use cyber attacks to promote political or social causes.
- Foreign governments: Engage in cyber warfare to gain strategic advantage or disrupt critical systems.
1.3 Impact of Cyber Attacks on Critical Infrastructures
- Power outages and disruption of electricity supply
- Intentional contamination of water supplies
- Disruption of transportation systems
- Communication failures leading to loss of coordination and information sharing
Chapter 2: Strengthening Defenses Against Cyber Attacks
2.1 Defense-in-Depth Approach
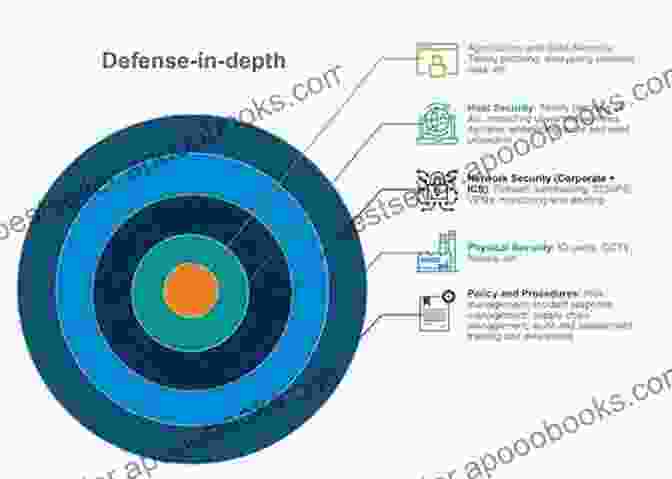
A defense-in-depth approach involves implementing multiple layers of security to create a comprehensive defense against cyber threats. This approach includes:
- Physical security measures (e.g., fencing, access control)
- Network security measures (e.g., firewalls, intrusion detection systems)
- Endpoint security measures (e.g., antivirus software, intrusion prevention)
- Employee awareness and training programs
2.2 Incident Response Planning and Procedures
Establishing clear incident response plans is essential for effectively handling cyber attacks. These plans should include:
- Steps for identifying and containing the threat
- Communication protocols for notifying stakeholders and coordinating response
- Procedures for restoring systems and data
- Assessment and lessons learned for future prevention
2.3 Advanced Security Technologies
- Artificial Intelligence (AI): Detect and respond to threats in real-time.
- Machine Learning (ML): Analyze threat patterns and predict future attacks.
- Blockchain: Secure and transparent record-keeping for incident management.
- Cybersecurity Mesh: Decentralized security architecture for enhanced resilience.
Chapter 3: Case Studies and Best Practices
3.1 Case Study: Stuxnet Attack on Iranian Nuclear Facilities
Stuxnet was a sophisticated cyber attack that targeted Iran's nuclear facilities. The attack highlights the potential consequences of cyber warfare on critical infrastructures and the importance of investing in defense systems.
3.2 Best Practices for Critical Infrastructure Protection
- Conduct regular cybersecurity audits and risk assessments.
- Implement a comprehensive incident response plan.
- Invest in advanced security technologies and continuous employee training.
- Collaborate with government agencies and industry partners to share information and best practices.
: Securing the Future of Critical Infrastructures
Protecting critical infrastructures from cyber attacks and cyber warfare zones is a complex and ever-evolving challenge. By understanding the threats, implementing comprehensive defense strategies, leveraging advanced technologies, and adopting best practices, we can strengthen our defenses and safeguard these essential systems.
Remember, the security of critical infrastructures is not just a matter of protecting individual systems but also safeguarding the well-being of our society and economy. By working together, we can ensure that our critical infrastructures remain resilient against the ever-present threat of cyber attacks.
4.6 out of 5
| Language | : | English |
| File size | : | 13512 KB |
| Print length | : | 363 pages |
| Screen Reader | : | Supported |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Emily Bunney
Emily Bunney Angela White
Angela White Anna Kovach
Anna Kovach Jessie Shedden
Jessie Shedden Jerri Daugherty
Jerri Daugherty Lenard D Moore
Lenard D Moore Anne Weil
Anne Weil Ilya Polyak
Ilya Polyak Ann Lauterbach
Ann Lauterbach Anitra Frazier
Anitra Frazier Tim Key
Tim Key Lynn Huggins Cooper
Lynn Huggins Cooper Mark Roncace
Mark Roncace Anna A Goodman
Anna A Goodman Robert Weintraub
Robert Weintraub Kelvin Young
Kelvin Young Anna Zapp
Anna Zapp John David Dingell
John David Dingell Haider Ala Hamoudi
Haider Ala Hamoudi Erik Jensen
Erik Jensen
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Davion PowellUnveiling the Horrific Truths: A Comprehensive Review of Chuck Palahniuk's...
Davion PowellUnveiling the Horrific Truths: A Comprehensive Review of Chuck Palahniuk's...
 Gavin MitchellGet Ready for a Heart-Pounding Ride with Chuck Palahniuk's "The Mobile Racing...
Gavin MitchellGet Ready for a Heart-Pounding Ride with Chuck Palahniuk's "The Mobile Racing... Fredrick CoxFollow ·9.7k
Fredrick CoxFollow ·9.7k Carl WalkerFollow ·10.8k
Carl WalkerFollow ·10.8k Roald DahlFollow ·19.2k
Roald DahlFollow ·19.2k Richard SimmonsFollow ·8.7k
Richard SimmonsFollow ·8.7k Bryson HayesFollow ·3.4k
Bryson HayesFollow ·3.4k Craig BlairFollow ·17k
Craig BlairFollow ·17k Dwayne MitchellFollow ·8.6k
Dwayne MitchellFollow ·8.6k Billy PetersonFollow ·13.9k
Billy PetersonFollow ·13.9k

 Marc Foster
Marc FosterUnveiling the Psyche of Soccer: Psychological,...
As the world...

 Stanley Bell
Stanley BellHope Draped in Black: A Haunting and Compelling Literary...
: Unveiling the Profoundity of Hope Draped...

 Jordan Blair
Jordan BlairUnleash the Power of Transformative Education: Exploring...
In the realm of education, where the seeds...

 Sam Carter
Sam CarterUnveiling the Enigmatic Realm of Reap the Shadows: Steel...
Immerse Yourself in a Tapestry of Mystery,...

 Jack Butler
Jack ButlerNatural Phenomena in Science and Myth: Unveiling the...
Throughout history, humans...
4.6 out of 5
| Language | : | English |
| File size | : | 13512 KB |
| Print length | : | 363 pages |
| Screen Reader | : | Supported |